User data is collected for various purposes. When visiting almost any website, you need to click the button labeled «Allow cookies» – it is available in social networks, marketplaces, cryptocurrency exchanges and news aggregators. In this way, developers legally collect information about the IP address from which users went to the site, geolocation, the amount of time spent on the page, visited sections and typed search queries. If you prohibit the transmission of this data, it can still be collected, but less legally. The history of Internet activity can be used to compile a dossier about a user in great detail. Anonymous browsers such as Tor can help reduce data leakage.

What is TOR
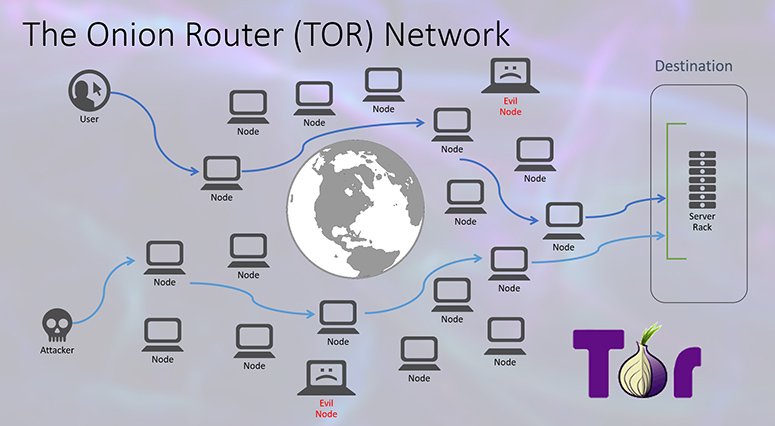
The Onion Router (TOR, Tor) — это особая технология для анонимного посещения сайтов в интернете. Ее используют в создании конфиденциальных сервисов или дубликатов заблокированных ресурсов — например, социальных сетей. Им присваивается доменное имя с окончанием .onion. Также TOR-технология используется в одноименном браузере для перехода в интернет.
Due to multi-stage encoding, the browser is slower than in usual web explorers. However, Tor is recommended when privacy is more important than speed.
Anonymity of crypto-transfers
With blockchain, it is possible to transfer money knowing only the wallet address. Cryptoenthusiasts position this as a privacy factor. But in practice, economic freedom and anonymity in transfers of digital assets are conditional. The blockchain records the data of all previous transactions.
The user’s identity is traceable, even though most blockchain wallets do not require a name, documents or phone number when registering. To leak information, it is enough to transfer assets from this vault to the balance of a centralized service, such as an exchange. After the transfer, the data from the profile will immediately refer to the wallet and the entire history of transactions. Such information is collected covertly and is not placed in the public domain. However, the data is stored on the platform’s servers. At the request of financial or law enforcement authorities, representatives of the exchange will disclose them.
How to protect anonymity with Tor
When working with crypto-payments, it is important to consider both sides of security. The first is to limit the hidden collection of information by services on the network. As previously mentioned, this is best handled by TOR technology. The second side is related to the wallet data exposed in the blockchain. In order to limit the ability to trace the original source of cryptoassets, special services for anonymous transactions are used.
How cryptomixers work?
Mixer services hide the sender’s wallet. With their help, users can transfer cryptocurrencies to any blockchain address without worrying about storage data leakage. Mixer services utilize mixing technology. Senders transfer assets to a special protocol (smart contract). The latter collects digital currency from several users, «mixes» it and outputs it to specified addresses.
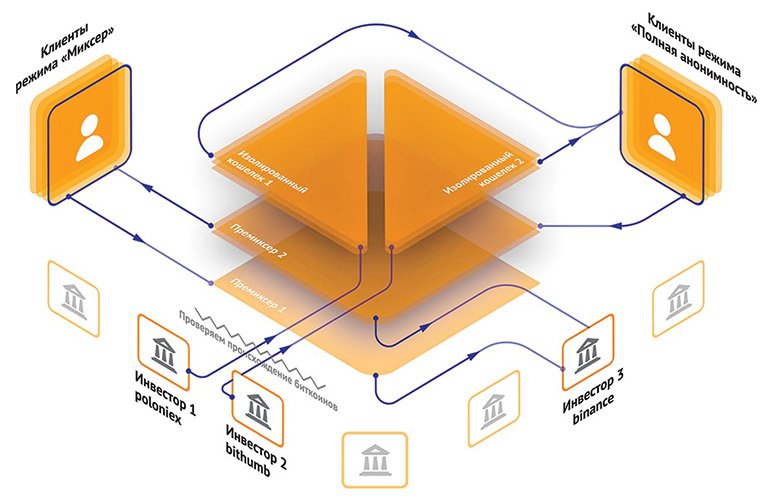
Depending on the method of «cleaning», the procedure can be instantaneous or take up to 6 hours. Despite the general principle of operation, anonymizer services can differ significantly.
First, most of the mixers are created for Bitcoin (BTC) crypto coin transactions. It will not be possible to mix different coins. There are also anonymizers for Ethereum.
This led to the emergence of centralized mixers. There is no question of complete anonymity in this case. To keep the data secret, you have to disclose it to an intermediary service. But this is considered a compromise solution. Such mixers are chosen by corporate holders who are concerned about their reputation and the impeccable origin of deposits.
There are also differences in blockchain technology for clearing assets. Without going into details, we can limit ourselves to the fact that they all lead to the main goal. Transactions on the blockchain remain anonymous.
How to make a transfer via cryptomixer
There are a few peculiarities that are important to know before making confidential transfers. In some modes, mixers transfer assets only from exchange accounts. Transactions between private wallets are also possible. For example, the Mixer.Money service offers 3 options.
The service is also available on the TOR-net. To transfer BTC coins with the highest measures of anonymity, you will need to perform several actions:
- Install TOR browser.
- Go to the Mixer.Money website.
- The most confidential option is to use the onion-version of the service.
- Select the desired anonymity mode.
- Specify the address of the recipient wallet.
- Click on the «Mix my bitcoin» button.
- Perform a transfer from your BTC wallet to the provided details.
- If necessary, you can save the letter of guarantee.
It is allowed to perform an anonymous transaction via Telegram bot. All transactions are carried out in automatic mode. The service has a support service. Therefore, you can get help if you have problems.
Detailed description of cryptomixers and advantages of each of them in our review.

